We provide assessment and certification services for abroad spectrum of cyber security services that meet the needs of companies required to certify to HIPAA, PCI DSS, HITRUST, SOC 2 Type II, ISO 27001, PCI PIN, PCI P2PE, PCI TSP, PA DSS, CSA STAR, GDPR, SWIFT, NIST 800-53 and FedRAMP. We are committed to empowering organizations in healthcare, financial markets, government contractors, education, and more develop and deploy strategic information security and compliance programs that are simplified, cost effective and comprehensive in both on-premise and cloud environments.
Our Team:
• Average experience of Security Assessors is more than 15 years.
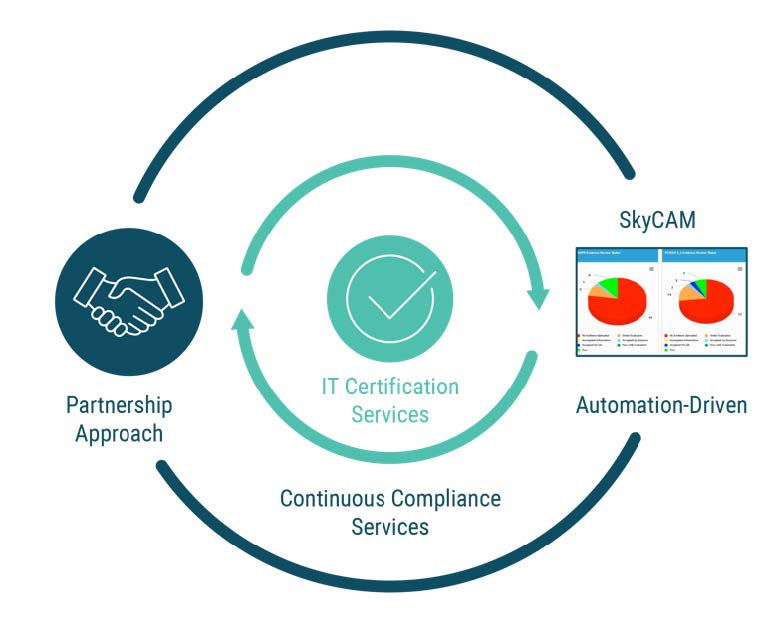
• We go “beyond a checklist auditor” and follow a consultative and partnership approach to help customers get compliant and remain complaint to HIPAA, SOC, PCI DSS and more.
• We provide, if needed by our clients, Continuous Compliance Quarterly Services which business can utilize as a package to help kick start compliance (and maintain compliance) instead of having to spend separately on security products and managed security services.
Our assessment methodology includes assigning a Compliance Assessor to each customer.
Qualified Security Assessor (QSA) – your expert who guides your Compliance journey
Partner with you to help you meet all compliance requirements
Explain to you what evidence is required for each compliance requirement
Evaluate the evidence provided
Work with internal Quality Assurance (QA) Team and Security Testing team to help you achieve compliance
QSA will be supported by a Project Manager (PMO) with the following responsibilities
✓ Track milestones including scoping, 50% pass, 100% pass of evidence and release of reports internally
✓ Escalate potential risks to meeting deadlines to management