Vulnerability Management for Dynamic IT Environments
![]()
Identify
Scan, identify and assess vulnerabilities across all assets (on-prem, cloud, mobile, virtual, container) within the organization
![]()
Prioritize
Prioritize vulnerabilities analyzing business impact and utilizing additional context from multiple third-party sources
![]()
Remediate
Remediate and report against numerous federal and industry-specific regulatory standards and benchmarks
![]()
End-to-End Management
Address every phase of the vulnerability management lifecycle – from assessment to remediation – eliminating the need for multiple, sometimes overlapping, solutions to address vulnerability management risks.
![]()
Zero-Gap Coverage
Discover and assess any IT resource in the organization including network, web, mobile, cloud and virtual infrastructures, reducing risk by ensuring that no assets are left unprotected.
![]()
Risk in Context
Make smart decisions and take the right actions to best secure the organization by providing a holistic view of enterprise-wide security, including risk from users, accounts and their privileges, and other security solutions such as SIEMs and firewalls
![]()
Deep Reporting and Analytics
Deep analytics and reporting delivered in a single dashboard ensures that all teams have the information and views they need to effectively manage application and asset risk
![]()
Integrated Scanning
Retrieve credentials with the highest level of privileges through native integration with Password Safe, improving the efficiency of scanning, and making scanning much more thorough than with other solutions available in the market.
![]()
Make Better Privilege Decisions
Automatically scan applications for vulnerabilities at run time to better inform IT and security teams on privileged access, enforcing quarantine, reducing application privileges, or preventing the launch of an application altogether based on policy.
Compliance Reporting
Simplify compliance reporting for COBIT, GLBA, HIPAA, HITRUST, ISO-27002, ITIL, MASS 201, NERC-FERC, NIST, PCI, SOX, and many more government and industry mandates with pre-built templates. Centralized reporting and an integrated data warehouse provides long term-trending, analytics and reporting for simple monitoring and streamlined regulatory compliance.
Configuration Benchmark Scanning
Streamline auditing and reporting against industry configuration guidelines and best practices with integrated templates for operating systems and applications from FDCC, NIST, STIGS, USGCB, CIS, and Microsoft. Audit configurations against internal policies, industry regulations, or recommended best practices.
Efficient and Effective Patch Management
Close the loop on vulnerabilities by providing seamless patching for Microsoft and third-party applications. Integrated, automated and agentless, the solution improves the efficiency and effectiveness of patch processes. Reduce the effort and expense by leveraging your existing WSUS or SCCM infrastructure for non-MSFT applications.
The Forrester Wave™: Vulnerability Risk Management, 2018
BeyondTrust Named a Leader in the 2018 Forrester Wave for Vulnerability Risk Management

Network Security Scanner
With over 10,000 deployments since 1998, BeyondTrust Network Security Scanner is the most sophisticated vulnerability assessment solution on the market. Available as a standalone application, a host-based option, or as part of the BeyondTrust Enterprise Vulnerability Management solution, Network Security Scanner enables you to efficiently identify IT exposures and prioritize remediation enterprise-wide.
Key Benefits
“What’s on my network?”
Today’s IT infrastructures are complex, with a mix of in-house physical and virtual systems, cloud-based environments, BYOD and a honeypot of networks derived from mergers and acquisitions. You may not know what is actually plugged into your networks and where the risks are. With agentless and optional agent technology, BeyondTrust can discover and assess all enterprise assets regardless of network complexity or device type.
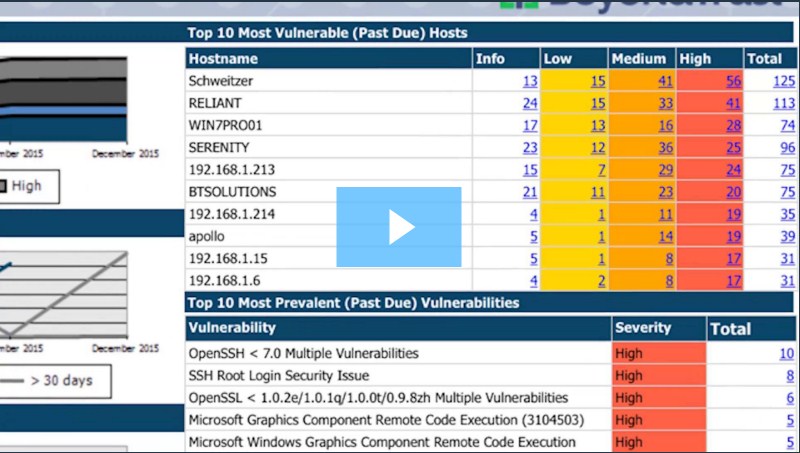
No more massive reports
Vulnerability reports can be overwhelming. Retina CS delivers unmatched reporting and analytics to help organizations quickly understand their risk and properly prioritize remediation efforts. The solution also includes BeyondInsight threat analytics capabilities that help identify anomalies associated with security risks, often buried and missed, within large volumes of scan data.
Prioritize remediation
Any vulnerability management tool can scan and produce a data dump of found vulnerabilities. Few extend beyond that silo to correlate vulnerable applications to those that are actually being used, on what systems and by what users. BeyondTrust provides this additional value, enabling organizations to focus their remediation efforts on applications that pose a higher risk as they are actively being used vs. those that may be part of a standard company image but seldom or never used.
Make auditors happy
Retina CS helps organizations identify, assess and manage IT risks associated with PCI, HIPPA, SOX, GLBA and several other compliance mandates. The solution makes it simple to demonstrate compliance via enumerated data mapping and automated report generation. Retina CS also provides compliance-driven dashboards to make it easy to respond to compliance violations.
Flexible Deployment Options
BeyondTrust solutions can be deployed on premise via software or hardware appliance, or hosted in the cloud through services including Amazon Web Services and Azure Marketplace.
Common Criteria Certified
Common Criteria is an internationally recognized set of guidelines created to insure a high and consistent standard for evaluating information security products. You can have confidence in the security of the products that have earned this certification through extensive independent lab evaluations, and avoid the cost and complexity of additional testing. Retina CS has earned Common Criteria Certification under an Evaluation Assurance Level (EAL)2+.

“Thanks to Retina, we’ve moved from a reactive security approach to a proactive security approach.”
Chief Information Officer, Gonzaga University
Recommended Resources

Whitepapers
The Forrester Wave™: Vulnerability Risk Management, 2018

Whitepapers
Sample Vulnerability Management Policy

Webcasts
The New Vulnerability and Risk Management (VRM) Paradigm: Holistic, Dynamic, Adaptive